How to Ensure Secure Hard Drive Destruction for Your Remote Workforce
How to Ensure Secure Hard Drive Destruction for Your Remote Workforce
In today’s digital world, safeguarding sensitive information is more important than ever—especially for remote workforces who rely on technology to connect, communicate, and collaborate.
Whether you’re an independent contractor, a manager of a dispersed team, or a business owner overseeing remote employees, ensuring secure hard drive destruction is essential to protecting your data from unauthorized access.
In this guide, we’ll explore why hard drive security matters, how to safely destroy hard drives, and what options are available for remote workers.
The Importance of Secure Hard Drive Destruction
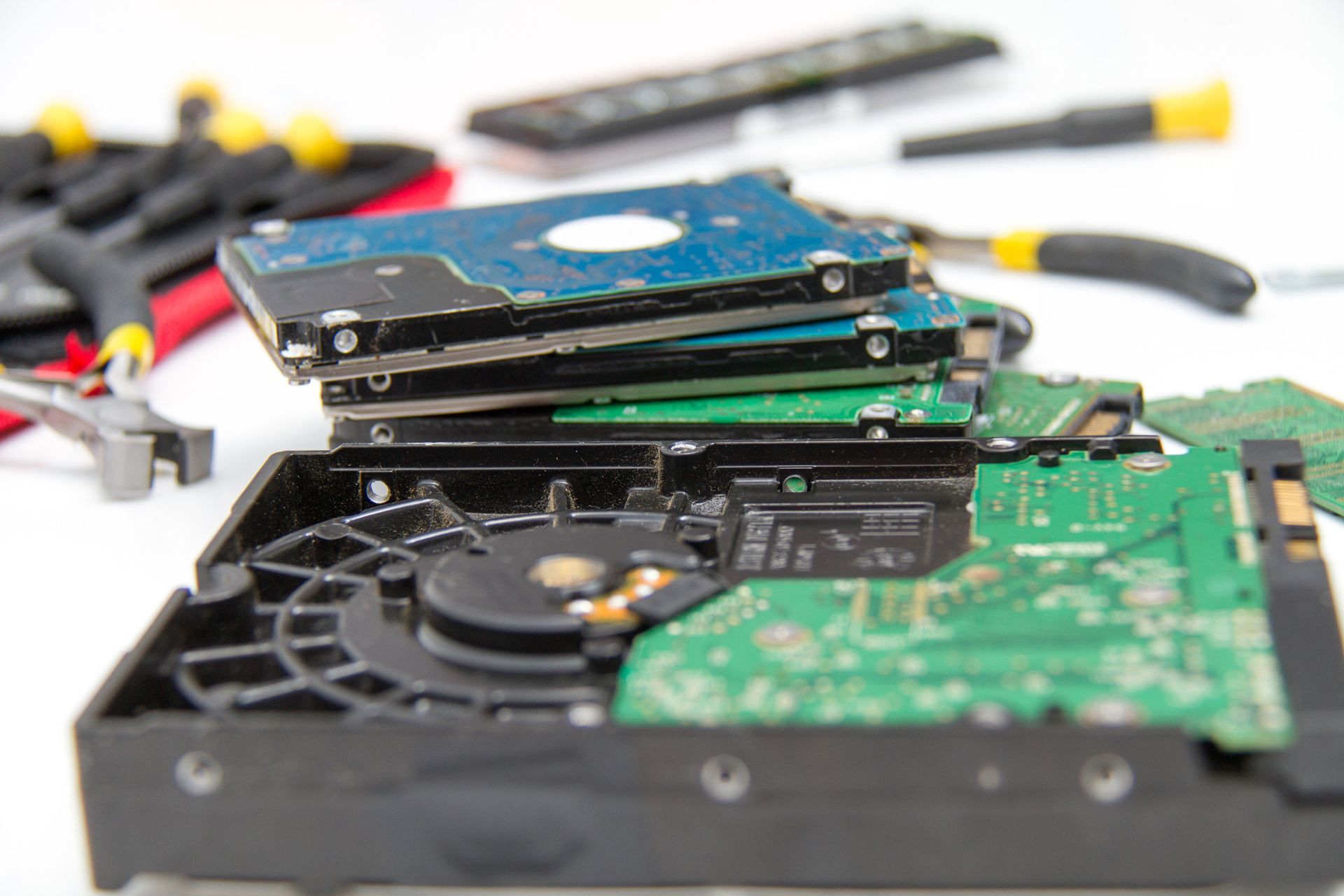
In the digital age, data breaches have become a pressing concern for organizations of all sizes. Remote workforces, in particular, face unique security challenges due to their decentralized nature. With sensitive information often stored on employees' personal devices, hard drive destruction becomes a critical aspect of data protection.
When a hard drive reaches the end of its life, simply deleting files isn’t sufficient. Deleted data can often be recovered using specialized software, posing a serious risk to your company’s security. Therefore, secure hard drive destruction is crucial to ensure that confidential information is permanently inaccessible.
Opting for professional data shredding services can provide peace of mind. These services use advanced techniques to physically destroy the hard drive, rendering data irretrievable. By choosing a reputable hard drive destruction company, you can rest assured that your data is in safe hands.
Understanding the Risks of Inadequate Destruction
Inadequate hard drive destruction can lead to severe consequences. If sensitive customer data, internal communications, or proprietary information falls into the wrong hands, it can result in financial loss, legal liabilities, and reputational damage. For remote workers, the stakes are even higher, as they often lack the same level of security infrastructure found in centralized office environments.
Cybercriminals are constantly developing new methods to exploit vulnerabilities, and discarded hard drives can be a goldmine of valuable information. Without proper destruction, even outdated devices can be used to extract sensitive data. This makes it imperative to adopt stringent measures for secure disposal.
Remote workers should be particularly vigilant about their data security practices, regularly reviewing and updating their protocols to mitigate potential risks. By understanding the dangers of inadequate hard drive destruction, individuals and businesses can take proactive steps to safeguard their information.
What Are the Best Practices for Hard Drive Disposal?
To ensure the secure disposal of hard drives, it’s essential to follow best practices. These practices not only protect your data but also streamline the destruction process for remote employees. Here are a few key recommendations to keep in mind:
First, perform regular data audits to identify obsolete devices. By keeping track of equipment, you can ensure that outdated devices are promptly decommissioned and destroyed.
Second, create a comprehensive data destruction policy that outlines procedures for securely disposing of hard drives. This policy should be communicated to all remote workers to maintain consistency.
Finally, consider utilizing residential document shredding services for remote employees. These services can provide on-site shredding options, allowing remote workers to securely destroy hard drives without leaving their homes. By following these best practices, you can enhance your data security and minimize the risk of breaches.
Evaluating Professional Data Shredding Services
Choosing the right data shredding services is a pivotal step in ensuring secure hard drive destruction. With various providers available, it’s important to evaluate your options carefully to find a service that meets your specific needs. Start by researching companies with a strong reputation and proven track record in the industry.
Look for a hard drive destruction company that offers transparent pricing and comprehensive service options. Some providers may offer additional services, such as electronic waste recycling, which can be beneficial for environmentally conscious organizations. Additionally, inquire about their chain-of-custody procedures to ensure that your data remains secure throughout the destruction process.
Finally, review customer testimonials and seek recommendations from peers to gauge the reliability and effectiveness of a provider. By thoroughly evaluating your options, you can choose a data shredding service that aligns with your security requirements and organizational values.
What to Look for in a Hard Drive Destruction Company
Selecting a reputable hard drive destruction company is crucial to maintaining your data security. To ensure you choose the right provider, consider the following factors:
First, verify that the company is certified and compliant with industry standards. Certifications such as NAID (National Association for Information Destruction) indicate that the provider adheres to strict security protocols and best practices. Second, assess their equipment and technology to ensure they use cutting-edge methods for data destruction.
Additionally, inquire about their data handling procedures and request a detailed explanation of their chain-of-custody practices. Understanding how your data is managed from collection to destruction is vital for ensuring its security. Finally, consider their customer service and support offerings, as responsive communication can make a significant difference in your experience.
How to Ensure Compliance with Data Protection Regulations
In today’s regulatory landscape, compliance is a top priority for organizations. When it comes to hard drive destruction, businesses must ensure compliance with data protection regulations to avoid penalties and legal liabilities. Familiarize yourself with relevant regulations, such as GDPR (General Data Protection Regulation) and HIPAA (Health Insurance Portability and Accountability Act), to understand your obligations.
Implementing a formal data destruction policy is a key step in achieving compliance. This policy should outline protocols for securely destroying hard drives and other electronic devices, and it should be regularly reviewed and updated to reflect changes in regulations. Providing training and resources to remote workers can also support compliance efforts.
Consider partnering with a certified hard drive destruction company that understands the regulatory landscape and can help you meet your compliance requirements. By prioritizing compliance, you can protect your organization from potential risks and maintain the trust of your stakeholders.
The Role of Tasting Notes in Data Security
While tasting notes are often associated with gourmet experiences, they can also play a role in data security. Just as tasting notes provide insight into the flavors and characteristics of a product, documenting your data destruction process offers transparency and accountability.
Maintaining detailed records of your hard drive destruction activities, including dates, methods, and responsible parties, can serve as a valuable resource in the event of an audit or inquiry. These records demonstrate your commitment to data security and provide evidence of your efforts to protect sensitive information.
By incorporating the concept of tasting notes into your data security practices, you can enhance your organization’s credibility and reinforce your dedication to
safeguarding confidential data.
Building a Community of Security-Conscious Remote Workers
Data security is a collective responsibility, and fostering a community of security-conscious remote workers can strengthen your organization’s defenses. Encourage open communication and collaboration among employees, creating a culture where data protection is prioritized.
Offer training and resources to help remote workers understand the importance of secure hard drive data destruction and other security practices. Regularly share updates and best practices to keep them informed about evolving threats and solutions.
By building a sense of community and shared responsibility, you can empower remote workers to actively contribute to your data security efforts. Together, you can create a united front against potential threats and ensure the continued protection of your organization’s information.
Conclusion Ensuring the Future of Secure Remote Work
As remote work continues to evolve, so too must our approach to data security. Secure hard drive destruction is a critical component of safeguarding sensitive information and mitigating risks.
By understanding the importance of proper destruction methods, evaluating professional services, and fostering a security-conscious community, you can protect your organization from potential threats.
Ready to destroy your data securely?
At Data Shredder Corporation, we understand how crucial it is to destroy sensitive data securely and recycle e-waste recycling in Massachusetts. We're here to offer you the best data destruction, hard drive shredding, and recycling services in Massachusetts, ensuring your peace of mind while contributing to the planet's health.
Your trust is our top priority, and we're dedicated to safeguarding your information with our certified, dependable solutions. Before a security breach even whispers your name, give us a call at(508) 978-4906 or fill out our
contact form.

Contact Us
40 School Street, 2nd Floor
Framingham, MA 01701
Email: service@datashredder.net
Business Hours
- Mon - Fri
- -
- Sat - Sun
- Closed









Share On: